Scientist.Net
Really like the looks of this project from Phil Haack - Scientist.Net
It allows for running two versions of code (in live) and comparing the results to each other. It's aimed at making refactoring safer by allowing you to ensure that your new path is producing the same results as the existing - while only the existing is used.
Integration Testing with .Net Core
This Integration Testing article provides advice on running integration tests for ASP.Net Core. It introduces the Test Host - a host specifically for integration testing.
EF Core Testing
This Testing with InMemory article shows how to use the InMemory provider with EF Core for integration tests.
Blog migration
I've started work on splitting the blog "content" from the red-folder.com website code (although this is likely to be put to one side due to other commitments).
Part of the intended solution is to trigger the publishing off a Github repo change (where I will store the content).
Now I wanted to put into place a BDD (SpecFlow) end to end test that would simulate the entire process. To do this I wanted to be able to automatically generate a fake blog into a test repo.
This GitHub Commit article was perfect for showing me how to do it.
I now have a SpecFlow test, hooked into the docs.functions VTST build process, which generates a fake blog into red-folder.docs.staging repo.
It doesn't do a lot more than that at the moment, but it's a great starting point.
Bot Prevention
My progress to date with the Ethical Hacking learning path came in handy this week. I've been looking to provide advice to a client on how to defend against Bot abuse.
As with most things security, the more I look the more concerned I get.
I already knew that there where services out there to solve captcha like bot checks for you. What I hadn't realised was just how easy and cheap it was. We are talking sub pence for a captcha response. If you do a goolge search for captcha solvers you will find a bus load. And they all look like legitimate services. Scary stuff.
In my advice, I talk about how to think like a bot master - how much will your defence inconvenience me?
I summarise the advice with the following facts:
- If it can be done by a human, it can be automated by a bot
- Attacks will have a financial ROI – cost of the bots vs the rewards
- Running a bot can be exceptionally cheap
- More security barriers, the more expensive that becomes
- Attacks can’t be stopped – just made too expensive to be viable
- It’s an arms race
I suspect I'll use some of this information on a second ROI article on security in the future. All good (but scary) stuff.
Ethical Hacking progress
Ok, another big jump in progress completed (helps if I don't update the blog for a while).
I still may struggle to complete by the end of the month, but it's looking close. Now at 82% of the Pluralsight Ethical Hacking Path.
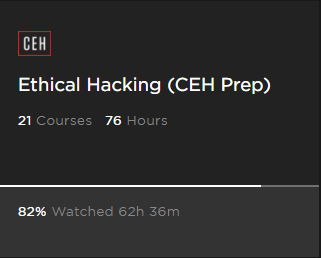
Breakdown of courses covered;
Contractor Process
Started to update by CV in line with my normal renewal process. I'll also be making some updated to the website & LinkedIn over the next week or so.